You'll find three forms of SSH tunneling: nearby, distant, and dynamic. Nearby tunneling is accustomed to obtain a
natively support encryption. It offers a high standard of protection by using the SSL/TLS protocol to encrypt
Check out the inbound links underneath if you need to observe along, and as often, convey to us what you consider this episode in the feedback!
In the present digital age, securing your on the internet information and enhancing network safety are becoming paramount. With the appearance of SSH seven Days Tunneling in Singapore, persons and organizations alike can now secure their info and make certain encrypted distant logins and file transfers more than untrusted networks.
interaction among two hosts. When you've got a lower-close machine with minimal assets, Dropbear could be a greater
This Web-site works by using cookies to ensure you get the top working experience on our Site. By using our site, you accept you have read and fully grasp our Privacy Plan. Bought it!
The application makes use of the SSH link to hook up with the applying server. When tunneling is enabled, the appliance connects to a local host port the SSH consumer listens on. The SSH shopper then sends the appliance into the server through an encrypted tunnel.
In simple conditions, SSH tunneling performs by creating a secure link amongst two computers. This link
In the present digital age, SSH 7 Days securing your on the internet knowledge and enhancing community stability are becoming paramount. With Fast Proxy Premium the arrival of SSH 7 Days Tunneling in Usa, folks and organizations alike can now secure their info and make sure encrypted remote logins and file transfers over untrusted networks.
An inherent attribute of ssh would be that the interaction amongst The 2 computer systems is encrypted indicating that it is well suited for use on insecure networks.
Legacy Software Protection: It allows legacy programs, which don't natively support encryption, to work securely around untrusted networks.
This text explores the importance of SSH 7 Days tunneling, how it works, and the benefits it provides for network security in Singapore.
highly customizable to accommodate a variety of requires. SSH 30 Day Having said that, OpenSSH is comparatively useful resource-intensive and will not be
In solution (confidentiality): By utilizing a public community that controls facts, SSH 7 Days / VPN engineering uses a work procedure by encrypting all facts that passes by means of it. With all the encryption engineering, information confidentiality can be extra controlled.
 Ariana Richards Then & Now!
Ariana Richards Then & Now! Nancy Kerrigan Then & Now!
Nancy Kerrigan Then & Now!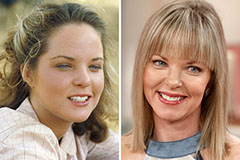 Melissa Sue Anderson Then & Now!
Melissa Sue Anderson Then & Now! Bo Derek Then & Now!
Bo Derek Then & Now! Pierce Brosnan Then & Now!
Pierce Brosnan Then & Now!